
A single data breach in contract management can expose thousands of confidential agreements, trade secrets, and personally identifiable information within minutes. Organizations increasingly rely on AI-driven contract platforms to manage their most sensitive business relationships, creating complex security challenges that demand sophisticated protection measures.
Contract data represents some of the most valuable information in any organization. These documents contain pricing strategies, intellectual property terms, customer information, and competitive advantages that could devastate a business if compromised. When artificial intelligence processes this data, the security stakes become even higher.
Key takeaway: AI-driven contract management platforms require multi-layered security approaches that address both traditional cybersecurity threats and AI-specific vulnerabilities to protect business-critical information.
Why Data Security Is Critical in AI-Driven Contract Management
Contract management platforms handle extraordinarily sensitive information. A typical enterprise contract database contains pricing negotiations, vendor relationships, compliance obligations, and proprietary business terms that competitors would pay significant sums to access.
AI amplifies both the value and vulnerability of this data. Machine learning algorithms analyze contract patterns to identify cost-saving opportunities, predict renewal outcomes, and automate compliance monitoring. However, these same algorithms require access to vast amounts of contract data, creating expanded attack surfaces and new security considerations.
Financial impact of contract data breaches:
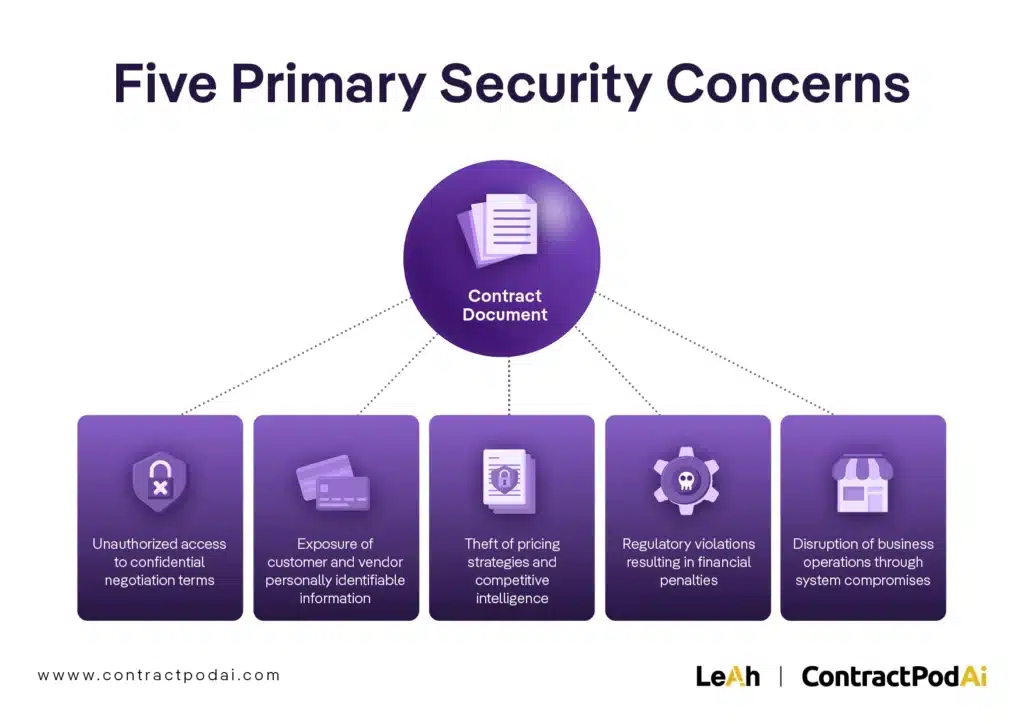
The financial impact of contract data breaches extends beyond immediate costs. Organizations face regulatory penalties, litigation expenses, competitive disadvantages, and long-term reputation damage. Primary security concerns include:
- Unauthorized access to confidential negotiation terms
- Exposure of customer and vendor personally identifiable information
- Theft of pricing strategies and competitive intelligence
- Regulatory violations resulting in financial penalties
- Disruption of business operations through system compromises
Core Data Protection Challenges in AI Contract Management
AI-driven contract platforms face unique security challenges that traditional document management systems don’t encounter. Understanding these challenges helps organizations implement appropriate protection measures.

Data Volume and Complexity
AI systems require extensive datasets to function effectively. Contract management platforms typically store thousands of documents with varying sensitivity levels, from routine purchase orders to merger agreements worth billions of dollars. This volume makes comprehensive security monitoring difficult while creating multiple potential breach points.
Multi-User Access Requirements
Contract management involves diverse stakeholders including legal teams, procurement professionals, executives, and external partners. Each group requires different access levels to perform their responsibilities, creating complex permission structures that must balance usability with security.
Integration Vulnerabilities
Modern contract platforms integrate with CRM systems, ERP platforms, e-signature tools, and financial systems. Each integration point represents a potential security weakness that attackers can exploit to access contract data or move laterally through organizational systems.
Organizations must carefully evaluate contract management integration security to ensure that connected systems don’t create vulnerabilities that compromise the entire contract ecosystem.
AI-Specific Risks
Machine learning models trained on contract data can inadvertently memorize and expose sensitive information. GenAI vs traditional machine learning systems present different risk profiles, with generative AI potentially creating new vulnerabilities through hallucinations or data reconstruction.
Additionally, AI systems may make decisions based on biased or incomplete data, potentially creating compliance violations or unfair contract terms. Understanding whether artificial intelligence will replace jobs helps organizations balance automation benefits with human oversight requirements.
Essential Data Security Measures for AI Contract Platforms
Effective contract platform security requires multiple layers of protection working together to create comprehensive defense against various threat types.
Advanced Encryption Technologies
Encryption at Rest

All contract data should be encrypted using AES-256 encryption when stored in databases or file systems. This ensures that even if attackers gain physical access to storage systems, the contract information remains unreadable without proper decryption keys.
Leading platforms implement transparent data encryption that automatically encrypts and decrypts information without impacting system performance. Database-level encryption protects against insider threats and provides additional security for backup systems.
Encryption in Transit
Contract data moving between systems, users, and integrated applications must be protected using Transport Layer Security (TLS) 1.3 or higher. This prevents attackers from intercepting contract information during transmission across networks.
Modern platforms also implement certificate pinning and perfect forward secrecy to ensure that encrypted communications remain secure even if encryption keys are compromised in the future.
Key Management Systems
Encryption is only as strong as key management practices. Enterprise-grade contract platforms use hardware security modules (HSMs) or cloud-based key management services to generate, store, and rotate encryption keys securely.
Proper key management includes regular key rotation, secure key storage, and controlled access to encryption keys separate from encrypted data.
Comprehensive Access Control Systems
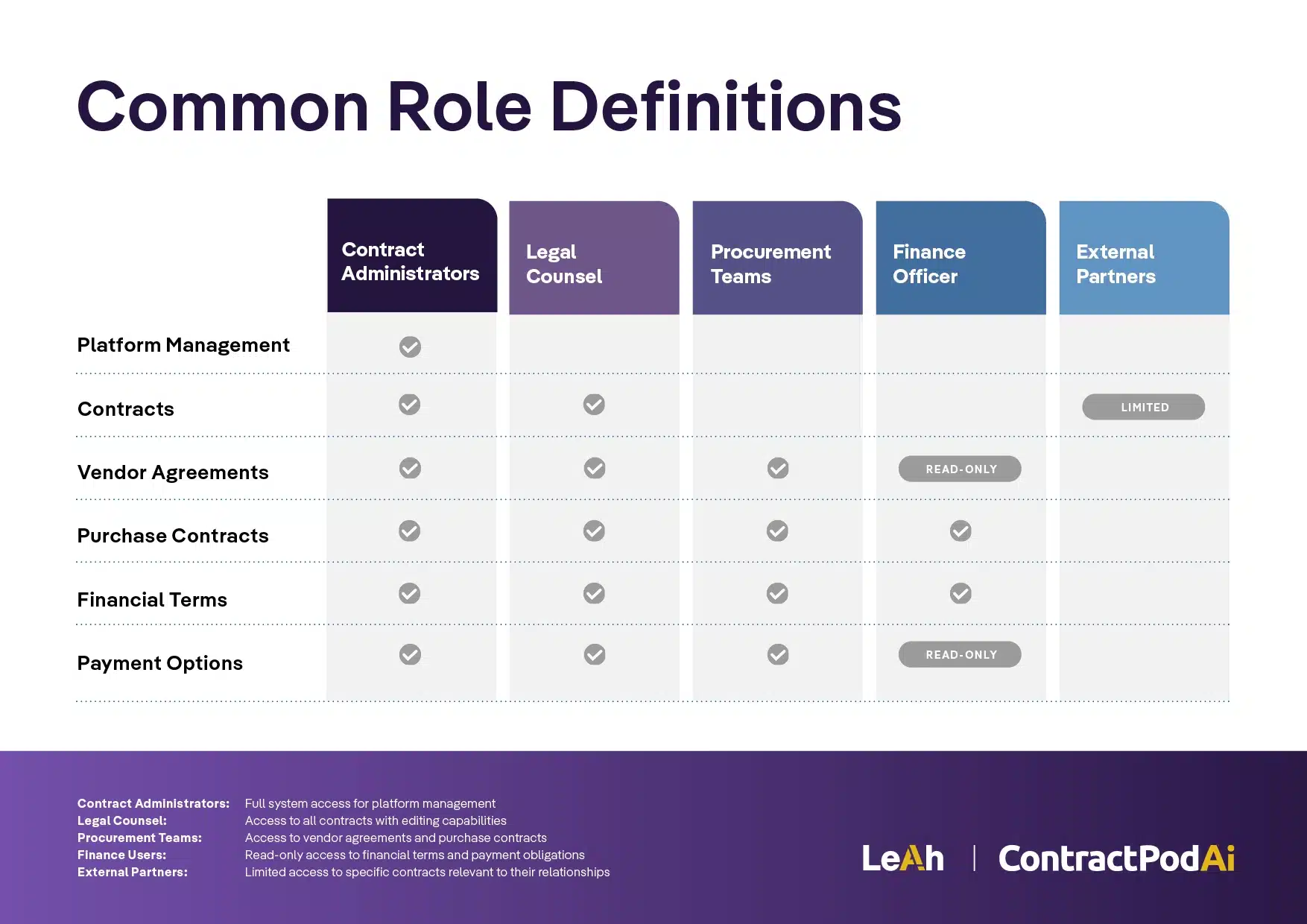
Role-Based Access Control (RBAC)
Effective contract security starts with ensuring users can only access information necessary for their job functions. RBAC systems assign permissions based on organizational roles rather than individual users, making permission management more scalable and consistent.
Common role definitions:
- Contract Administrators: Full system access for platform management
- Legal Counsel: Access to all contracts with editing capabilities
- Procurement Teams: Access to vendor agreements and purchase contracts
- Finance Users: Read-only access to financial terms and payment obligations
- External Partners: Limited access to specific contracts relevant to their relationships
Attribute-Based Access Control (ABAC)
Advanced platforms implement ABAC systems that consider multiple factors when granting access, including user role, contract sensitivity level, time of access, and geographic location. This provides more granular control than traditional role-based systems.
Multi-Factor Authentication (MFA)
All platform access should require MFA, combining something users know (passwords), something they have (mobile devices or security tokens), and potentially something they are (biometric identifiers). This significantly reduces the risk of unauthorized access even if passwords are compromised.
Secure Storage and Infrastructure
Cloud Security Configurations
Organizations using cloud-based contract platforms must ensure proper security configurations. This includes enabling logging and monitoring, configuring network access controls, and implementing backup and disaster recovery procedures.
Cloud platforms should maintain compliance certifications including SOC 2 Type II, ISO 27001, and industry-specific standards relevant to the organization’s regulatory requirements. When choosing the best CLM software, organizations should prioritize vendors with comprehensive security certifications and transparent security practices.
Network Segmentation
Contract management systems should operate in isolated network segments with carefully controlled access points. This limits potential damage if other organizational systems are compromised and provides additional monitoring capabilities for contract-related activities.
Regular Security Assessments
Continuous security monitoring identifies potential vulnerabilities before they can be exploited. This includes automated vulnerability scanning, penetration testing, and security code reviews for custom integrations or configurations.
Regulatory Compliance in AI Contract Management

Contract management platforms must comply with various data protection regulations that vary by industry and geographic location.
GDPR Requirements
The General Data Protection Regulation affects any organization processing personal data of EU residents. Contract platforms must implement:
- Data Minimization: Only collect and process personal data necessary for contract management purposes
- Right to Erasure: Provide mechanisms to delete personal data when contracts end or individuals withdraw consent
- Data Portability: Allow individuals to export their personal data in machine-readable formats
- Privacy by Design: Build privacy protections into system architecture rather than adding them as afterthoughts.
CCPA Compliance
The California Consumer Privacy Act provides similar protections for California residents. Contract platforms must disclose data collection practices, provide opt-out mechanisms, and implement consumer rights requests.
Industry-Specific Regulations
Different industries face additional compliance requirements:
- Healthcare (HIPAA): Contracts containing protected health information require additional security measures and audit capabilities
- Financial Services (SOX, PCI DSS): Financial contracts must maintain detailed audit trails and meet specific data protection standards
- Government Contractors (FedRAMP, DFARS): Organizations working with government agencies must meet federal security requirements
Best Practices for Secure AI Contract Management
Implementing comprehensive security requires combining technology solutions with operational procedures and organizational policies.
Implement Zero-Trust Architecture
Zero-trust security assumes that no user or system should be trusted by default, regardless of their location or credentials. Every access request must be verified and authorized based on current context and risk factors.
Zero-trust principles for contract management:
- Verify user identity for every access request
- Validate device security before granting access
- Monitor and log all contract-related activities
- Apply least-privilege access principles consistently
- Regularly review and update access permissions
Develop Incident Response Procedures
Security incidents in contract management can have severe business impacts. Organizations need clear procedures for detecting, containing, and recovering from security breaches.
Effective incident response plans include:
- Clear escalation procedures for different threat levels
- Communication protocols for internal teams and external partners
- Data breach notification procedures to meet regulatory requirements
- Recovery procedures to restore normal operations quickly
- Post-incident analysis to improve future security measures
Modern contract management platforms like ContractPodAi provide comprehensive audit trails and logging capabilities that support incident response efforts and help organizations meet regulatory notification requirements.
Regular Security Training
Human error remains a leading cause of security breaches. Regular training helps users understand their role in protecting contract data and recognize potential security threats. Avoiding common mistakes in contract management through proper training significantly reduces security risks.
Training topics should cover:
- Password security and MFA best practices
- Phishing and social engineering recognition
- Proper data handling procedures
- Incident reporting requirements
- Regulatory compliance obligations
Leading contract management platforms provide user education resources and built-in security guidance to help organizations maintain strong security practices across their teams.
Vendor Risk Management
Organizations using third-party contract management platforms must evaluate vendor security practices and monitor ongoing compliance. This includes reviewing security certifications, conducting security assessments, and establishing clear contractual requirements for data protection. Organizations with understaffed security teams face an average of $1.76 million in higher breach costs compared to those with adequate staffing levels.
When considering CLM software buying tips, security should be a primary evaluation criterion alongside functionality and cost considerations.
Risk Mitigation Strategies
Even with comprehensive security measures, risks remain. Organizations need strategies to minimize the impact of potential security incidents.
Data Backup and Recovery
Regular backups ensure that contract data can be recovered if systems are compromised or damaged. Backup systems should be isolated from production environments and regularly tested to ensure recovery procedures work effectively.
ContractPodAi implements robust backup and disaster recovery procedures with daily and hourly database backups, daily file server backups, and cross-regional replication to ensure data availability and business continuity.
Cyber Insurance
Cyber insurance helps organizations manage the financial impact of security breaches, including legal costs, regulatory penalties, and business interruption expenses. However, insurance should supplement, not replace, proper security measures.
When evaluating cyber insurance options, organizations should consider platforms that already implement comprehensive security measures, as this can often result in better coverage terms and lower premiums due to reduced risk profiles.
Business Continuity Planning
Security incidents can disrupt contract management operations, potentially affecting critical business relationships. Continuity plans should address how organizations will maintain essential contract processes during security incidents or system outages.
Modern cloud-based contract management platforms like ContractPodAi are designed with high availability architecture and redundant systems that help minimize disruption during incidents and support business continuity objectives.
ContractPodAi’s Security Approach

ContractPodAI implements enterprise-grade security measures through its subscription software-as-a-service built on Microsoft Azure Cloud infrastructure, maintaining a 99.9% uptime commitment (excluding scheduled maintenance periods). The platform integrates Leah™ Standalone, an innovative agentic AI-powered legal solution, within a comprehensive contract management ecosystem designed for maximum security and performance.
Enterprise Cloud Infrastructure
The CPAi Service operates regionally within Microsoft Azure Cloud datacenters across continental United States, continental Europe, and Australia. Each hosting location is mirrored across multiple, geographically dispersed data centers for fault tolerance and business continuity. Clients may select specific regional processing locations upon implementation, with available deployments including North Continental Europe (Ireland) replicated to West Europe (Netherlands), East US replicated to West US, and Australia East replicated to Australia Central.
Advanced Encryption Standards
ContractPodAI employs comprehensive encryption across all data touchpoints:
- Transport Layer Security: TLS encryption technology for all data transfers, with connections negotiated for at least 256-bit encryption or stronger and private keys of at least 2048 bits
- Data at Rest: Database instances encrypted at rest using industry-standard encryption for additional data security layer
- PII Protection: Certificate key encryption specifically implemented for personally identifiable information
- Azure Storage Encryption: Enabled for all storage accounts and cannot be disabled, ensuring data is secured by default without requiring code modifications
Multi-Layered Access Controls
The platform implements sophisticated identity and access management:
- Identity Management: Users require valid username and password authentication, with user profiles containing comprehensive access controls through User Groups, Security Roles, and Profile Rules
- Single Sign-On: SAML 2.0 integration available for enhanced user administration and security controls
- Administrative Access: Limited to select ContractPodAI operations team members who complete successful background checks, security awareness training, and acknowledge privacy and confidentiality agreements
- Network Access: Multi-factor VPN or Private Proxy connections with additional authentication, authorization, and accounting through standard security mechanisms
- Data Isolation: Each subscriber maintains their own unique, credentialed, and named database instance with subscriber data never commingled between tenants
Comprehensive Security Infrastructure
ContractPodAI leverages multiple security technologies and processes:
- Anti-Virus and Anti-Malware: Best-in-class tools monitor and block virus and malware behavior, including protection against emerging threats beyond traditional signature-based solutions
- Firewall Protection: Managed firewalls implement layered security approach with strict ingress and egress policies based on protocol, port, source, and destination, discarding unauthorized traffic at the Internet boundary
- Intrusion Prevention: Host-based intrusion prevention and monitoring systems deployed at server and network layers
- Vulnerability Management: Enterprise-class program monitors and alerts on unauthorized changes or security configurations with services undergoing third-party penetration tests annually or prior to material changes
Rigorous Compliance and Monitoring
The platform maintains comprehensive compliance standards:
- SOC 2 Type II Certification: Annual independent evaluation of information security control environment covering security, availability, and confidentiality
- GDPR Compliance: Data Processing Addendums including Standard Contractual Clauses approved by the European Commission, incorporating Article 28 requirements
- HIPAA Compliance: Business Associate Agreements (BAAs) available to meet healthcare client requirements
- 24/7 Security Response: Dedicated security team available around the clock with rigorous incident management process for events affecting confidentiality, integrity, and availability
- Customer Communication: Immediate notification and investigative support provided if incidents involve customer data
Advanced Backup and Disaster Recovery
ContractPodAI implements robust data protection and business continuity measures:
- Point-in-Time Recovery: Azure point-in-time restore capability enabled for recovery to any instant within the prior 30 days using daily snapshots and transaction log backups
- Long-Term Protection: Nightly Azure snapshots for extended recoverability with Azure Backup Service snapshot functionality for daily blob storage protection
- Geographic Redundancy: Data centers built in clusters across various regions with automated failover processes moving customer traffic away from affected areas
- Backup Retention: Both database and file backups encrypted and retained for one year with geographically diverse operations staff ensuring business continuity during office disruptions
Physical and Network Security
Processing occurs within Microsoft Azure data centers featuring:
- Physical Access Control: Nondescript facilities with professional security staff controlling access at perimeter and building ingress points
- Surveillance Systems: Video monitoring and intrusion detection at minimum of all ingress and egress points
- Multi-Factor Authentication: Authorized staff must pass two-factor authentication minimum twice to access data center floors
- Visitor Management: All visitors and contractors required to present identification, sign in, and receive continuous escort by authorized personnel
- Network Infrastructure: Low latency availability through Azure’s region and availability zone architecture with redundant power, networking, and connectivity housed in separate facilities
AI-Enhanced Security with Leah Integration
The Leah™ Standalone architecture utilizes Azure-managed services within a secure, multi-tenant SaaS environment:
- Containerized Applications: Web applications deployed in Azure App Service using Docker with FastAPI backend for document processing and NLP tasks
- Secure AI Processing: Integration with Azure OpenAI, OpenAI, and Google Cloud AI through unified orchestration layer with JWT-based security and tokenized interactions
- Vector Search Security: Qdrant vector store for semantic search with tenant-specific isolation and encrypted data handling
- Document Processing: Secure file access through Azure Blob Storage with Shared Access Signatures for controlled anonymous uploads
This comprehensive security framework ensures ContractPodAI’s platform meets enterprise standards for protecting sensitive contract data while enabling advanced AI capabilities and maintaining the performance required for modern legal and business operations.
Ready to enhance your contract security? Learn more about ContractPodAi’s comprehensive security features and discover how AI-driven contract management can protect your organization’s most valuable agreements while streamlining operations.
FAQs
The biggest risk is unauthorized access to sensitive contract data through compromised user accounts or system vulnerabilities. AI systems process vast amounts of confidential information, making them attractive targets for cybercriminals seeking trade secrets, pricing strategies, or personally identifiable information.
Encryption protects contract data by converting it into unreadable code that can only be decrypted with proper keys. AI platforms use AES-256 encryption for data at rest and TLS 1.3 for data in transit, ensuring contract information remains secure even if storage systems or network communications are compromised. Learn more about contract management software security best practices.
Key regulations include GDPR for European data protection, CCPA for California residents, HIPAA for healthcare information, and industry-specific requirements like SOX for financial services. Organizations must ensure their platforms meet all applicable regulatory requirements for their industry and geographic location. Consider defining your CLM solution needs to include compliance requirements.
Modern AI-powered security systems monitor user behavior patterns, network activity, and data access patterns to identify potential threats. These systems establish baseline behaviors and alert security teams when activities deviate from normal patterns, such as unusual login locations or bulk document downloads. Breaches involving stolen or compromised credentials take an average of 292 days to identify and contain, making early detection crucial. Contract management analytics play a crucial role in threat detection.
Organizations should immediately activate their incident response plan, which includes containing the breach, assessing the scope of compromised data, notifying relevant stakeholders and regulatory authorities, and implementing recovery procedures. Post-incident analysis helps improve future security measures and prevent similar breaches. Understanding the legal front door concept helps organizations prepare comprehensive response strategies.


